
My earlier post discussed examples of high-profile malvertising campaigns as a starting point for exploring the malicious practice of deploying ads to infect computers. This note digs into the mechanics of malicious ads to better understand how they function and what they do.
One approach to conducting a malvertising campaign involves an image ad that people click on to visit the advertised website. In this context, the advertised website turns out to be malicious in itself or redirects to a malicious site. For example, Kimberly from StopMalvertising described one malvertisement that took the person viewing or clicking on the ad to popadscdn.net, which redirected to pop.biyoetanol.net, which redirected to ad.amiadrugaddict.info, which eventually redirected to the Blackhole Exploit Kit hosted at 0d1.cz.cc.
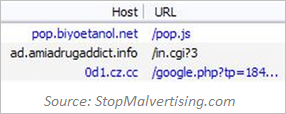
If redirected to a site hosting an exploit kit, the victim’s system is subjected to one or more attacks on the browser or the software that the browser can invoke, such as Acrobat Reader or Java Runtime. The exploit kit’s code probes the victim’s browser environment to determine which vulnerability to attempt exploiting. Some of the malicious sites implement another approach, relying on social engineering to trick the visitor into installing malicious software.
Malicious ads might also take the form of Flash programs. Flash provides the attacker with the ability to use ActionScript to embed “business logic” directly into the ad. This allows attackers to incorporate more elaborate instructions that would execute in the victim’s browser as soon as the advertisement is displayed.
For instance, the Flash-based ad can incorporate logic that decides when to attack the user and whom to attack. The ad might trigger a malicious action on a particular date; this is typically done to delay the attack until after the advertising network examined and approved the ad. For instance, the ad can begin redirecting victims to a malicious site only during a weekend, and may decide to only go after people in a particular location.
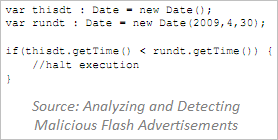
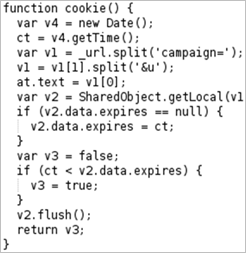
The Flash advertisement’s logic may also evade detection by only attacking the user once—such ads typically use a cookie-like Local Shared Object (LSO) to avoid attacking the user if he has already been targeted. These and other techniques are described in the paper Analyzing and Detecting Malicious Flash Advertisements by Ford, Cova, Kruegel and Vigna.
Since Flash executes in the victim’s browser as soon as the ad is displayed, Flash/ActionScript-based malvertisements provide attackers with more flexibility than those based on HTML/JavaScript. Perhaps the future will bring malvertising campaigns where Flash-based ads usurp the victim’s CPU cycles to run computations, such as distributed password cracking. Another potential is to use the browser for Bitcoin mining; such operations are already possible using pure JavaScript, so an ActionScript version isn’t that far off.
Attackers take advantage of the ad’s nature to direct people to the advertised website by advertising websites that turn out to be malicious. They do this by modifying the ad’s destination after submitting it to the advertising network. Using Flash programs to implement the banner ad provides the attacker with additional control over the attack logic, because Flash can incorporate ActionScript that tends to be harder to examine than JavaScript.
This note is part of a series of malvertising-related posts. You can also learn:
- Examples of Malicious Ad Campaigns
- How Malicious Ad Campaigns Are Protected
- How Malicious Ads Are Deployed
- Dealing With Malicious Ads - Who and How?