Incident responders and forensic investigators need to be careful when using 32-bit tools to examine file system artifacts on 64-bit Windows. Christian Wojner documented the issue in a paper titled The WOW-Effect. He demonstrated how the WOW64 File System Redirector built into 64-bit Windows transparently redirects 32-bit tools’ access to core OS directories and registry values. This is likely to confuse forensics personnel performing live analysis of the system.
Christian explained that “64‐bit versions of Windows provide backward compatibility for 32‐bit executables.” For instance, a 32-bit application accessing %windir%System32 will be transparently redirected by the OS to access a corresponding file in the %windir%SysWOW64 directory. “In other words, a 32‐bit application will never see any file stored in System32, it will always access SysWOW64 instead.”
Consider the situation, described in Christian’s paper, where the investigator uses the classic md5sum tool (which is usually 32-bit) to look at file that corresponds to a suspicious process…
On my 64-bit Windows 7 laboratory system, I called a demo file “myfile.exe” (0d07469c97791d2d51a6317f84f75025) and placed it in the C:WindowsSystem32 directory. I placed a different file (ec75883fdc02c259026e0585e720dfe7) under the same name in C:WindowsSysWOW64.
I used 32-bit md5sum to read the file from C:WindowsSystem32. The OS redirected the program to read from C:WindowsSysWOW64 without any visual indications that this occurred:
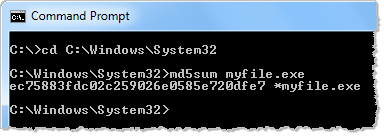
However, when I use a 64-bit tool for calculating the MD5 hash of the same file, I get a different value. This value corresponds to the actual file under C:WindowsSystem32 that I intended to examine:
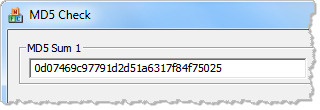
That’s because when the 32-bit md5sum program attempted to read C:WindowsSystem32myfile.exe, the OS transparently redirected it to C:WindowsSysWOW64myfile.exe.
You can see a video of my little demo on YouTube.
Christian pointed out another scenario that might mislead incident responders: It’s not uncommon for investigators to upload suspicious files to VirusTotal for malware scanning. However, if the investigator uses a 32-bit browser, then he or she will be uploading a different file than what would be uploaded using a 64-bit browser.
If you’re concerned about this issue, stick to using 64-bit tools when performing live analysis of 64-bit Windows systems. If you’re using 32-bit tools, there is another approach to accessing contents of C:Windows32, though this doesn’t work for other files and registry items that Windows might redirect. Instead of attempting to access %windir%System32, access %windir%Sysnative to avoid redirection. Thanks to Tyler Hudak for telling me about this:
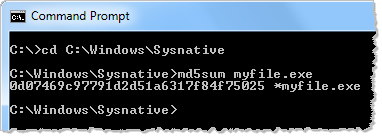
For more details and examples regarding this issue, see Christian’s The WOW-Effect paper.