Microsoft Office documents offer a convenient way to infect systems through the use of macros. However, the attacker needs to persuade victims to enable macros after opening the booby trapped file. Social engineering is an important aspect of these attack strategies.
The defense mechanism that such malware authors need to bypass is typically the yellow security warning that Microsoft Office applications display to explain that "Macros have been disabled." How would you persuade the document's recipient to click the enticingly-named Enable Content?
Misrepresent the Meaning of the Security Warning
One approach attackers have employed to deal with the warning involves convincing victims that the security message indicates that the document has been somehow secured to safeguard its contents. This is a clever way of using the pretext of security, which most users don't understand, to persuade individuals. Kimberly's post on the use of macro viruses presents several real-world examples that utilize this approach; these documents "explained" to victims:
- "Private text has been hidden to caution against unauthorized person. Click Enable Content"
- "Please enable macros to view secure document"
- "This is a locked document please click option to enable content"
As convincing as such text can be for some people, sometimes victims might require additional guidance to the activate macros.
Provide Detailed Instructions for Enabling Macros
Recognizing that some of the victims might not be tech-savvy, adversaries have been known to offer step-by-step instructions for enabling macros. This helps address scenario where the person's Microsoft Office is globally configured to disable all macros.
For instance, take the real-world malicious Word document described by Dmitry Bestuzhev. The file was called DIAN_caso-5415.doc. When victims opened this file, they saw a nicely-formatted message that the adversary embedded in the document, explaining why the content could not be shown. The text is in Spanish, because this file was sent to recipients in Spanish-speaking countries:
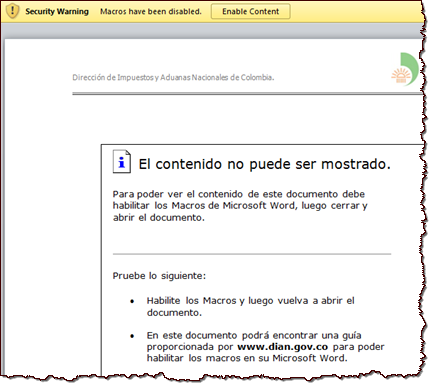
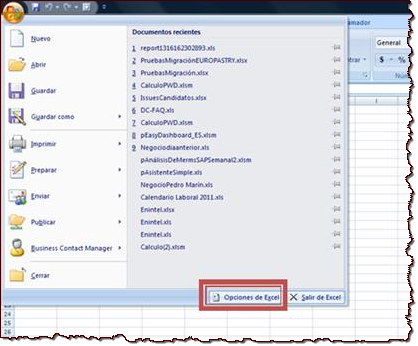
The text advised that to view the document's contents, the person need to enable macros. The malicious document included step-by-step instructions for accomplishing this. The instructions accommodated multiple versions of Microsoft Word and Excel and include detailed steps and screenshots like this:
If the Approach Works, Keep Using It
According to Dmitry, the document above was sent to victims in Colombia under the guise of a tax fraud notice. Interestingly, another malicious document that incorporated the same macro-enabling instructions was observed a month later by UNAM - CERT in Mexico. In that case, the context was a bank withdrawal notification. The file was called RETIRO-COMPRA_29882.doc.
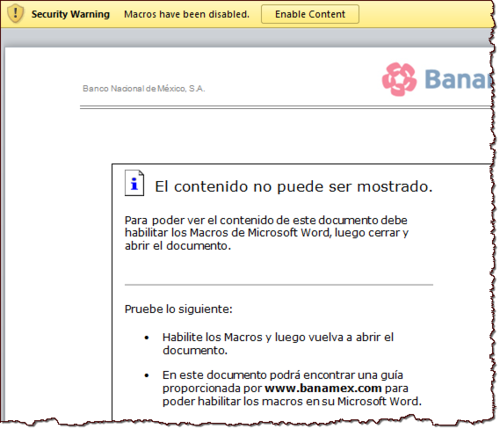
As I explained in an earlier post about SRP streams, the analysis of SRP streams in both files reinforces the notion that these documents were probably used by the same adversary to pursue victims in multiple Spanish-speaking countries, including Colombia, Mexico and Chile. In each case, the document was crafted to social-engineer the recipient to enable macros and allow the malicious code to infect the system.
If you're like to take a closer look at these two malicious documents, you can download them from the Malwr repository links I provided above for each file. Just be careful to conduct your examination on a properly-isolated laboratory system.