I don’t understand why Facebook decided to add one-time password (OTP) support for logging into its website. It’s less useful than it might appear. It is a first step towards a more meaningful security feature or just a ploy to obtain phone numbers of the social network’s users? Perhaps we can figure it out together.
The new OTP feature allows security-conscious Facebook users to request a one-time password prior to logging in from an untrusted system, such as an Internet kiosk. As a security guy, I love this, since it makes it harder for keyloggers to capture meaningful logon credentials. However, because this feature is optional and is a bit awkward to use, very few people will actually take advantage of it. What objective did Facebook have in mind, then, when implementing OTP?
Registering Your Mobile Number With Facebook
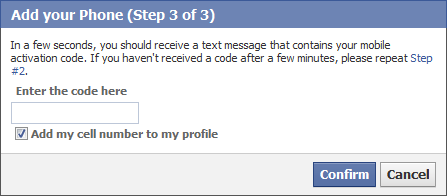
First, the Facebook user needs to associate his mobile phone number with Facebook. This is a one-time step, which involves going to the “Update your Security Information” screen and clicking “Sign up for Facebook mobile.”Facebook will ask you to send an SMS text message consisting solely of the letter “f” to 32665 (FBOOK) from your mobile phone. Facebook will respond with a code, which you’ll need to enter into the “Add your Phone” wizard.
Requesting a Facebook One-Time Password
Once your mobile number is registered with Facebook, you’ll be able to request a one-time password by texting the letters “otp” to 32665 (FBOOK) from your mobile phone. Facebook will respond with a message like this:
Your Facebook One-time password is 7KGWJNdf (valid for 20 min) Text your status to 32665 (FBOOK) to update.
You can now use the specified one-time password instead of your regular password to login to Facebook within the next 20 minutes.
Facebook OTP is Not Two-Factor Authentication
Larry Seltzer pointed out that the goal of most one-time password deployments is “to add a second factor to authentication, not to replace the one factor with a different single factor.” For instance, the banks that rolled out OTP for their customers wanted to add “something you have (your phone) to something you know (your password).” In contrast, “Facebook is doing this to save you from having to enter your password on a strange computer, not to strengthen authentication.”
As another point of reference, consider Google’s recent decision to support second factor authentication for Google Apps users. When enabled, this feature prompts the user for a one-time password in addition to the user’s regular password. Google can send a one-time password to the user’s mobile phone. Google also allows for one-time passwords to be generated in advance and using a phone app to support cases where the user has no wireless signal.
Why Use Facebook One-Time Passwords?
Most people don’t care about security, unless they stand a lot to lose should a breach occur. I suspect very few people will actually use Facebook’s OTP mechanism, because it’s simpler not to use it. In fact, Facebook’s recently-improved mechanism for reclaiming one’s hijacked account might encourage people to be more reckless, knowing that they’ll be easily able to get the account back should it be compromised.
I suppose some of the people who treasure their social network identities will have an incentive to guard their Facebook logon credentials. Also, those who have accumulated lots of Facebook credits will want to safeguard their virtual currency funds. I’m still skeptical, though: Even though PayPal and e-Trade provide OTP security tokens to their customers almost for free, not many actually take advantage of this option.
What Risks Is Facebook Mitigating?
According to Facebook, it provides OTP support “to make it safer to use public computers in places like hotels, cafes or airport.” Are keyloggers on public computers that capture Facebook credentials such a prevalent threat? It might be—I wish I had some data on this. The compromises of Facebook accounts I’ve seen fell into two different scenarios:
- User’s browser session cookies were stolen by malware to authenticate to Facebook as the victim (e.g., the Koobface worm)
- User inadvertently gave Facebook logon credentials as part of an email-based phishing scam
Facebook’s one-time password option isn’t designed to mitigate these risks. In fact, with the increasing adoption of smart phones, fewer people will want to login to Facebook from untrusted computers, since they’ll be interacting with the site from their mobile phone.
Then What’s The Point of Facebook One-Time Passwords?
I am skeptical that many people will take advantage of Facebook’s OTP feature. I’m also skeptical that the feature addresses the risks that most Facebook users worry about.
Facebook has been rolling out excellent security features, and that’s wonderful. I simply don’t see OTP as one of those features. Maybe it’s a first step towards support for actual 2-factor authentication? Or is it just a way for Facebook to encourage its users to share their phone numbers with Facebook? I’d love to hear your thoughts because, frankly, I am a bit lost on this one.